S4A debugging with avr-gdb and simavr
While this has been possible for a while in S4A, with long workarounds, it got a lot easier in the 5.0 beta IDE.
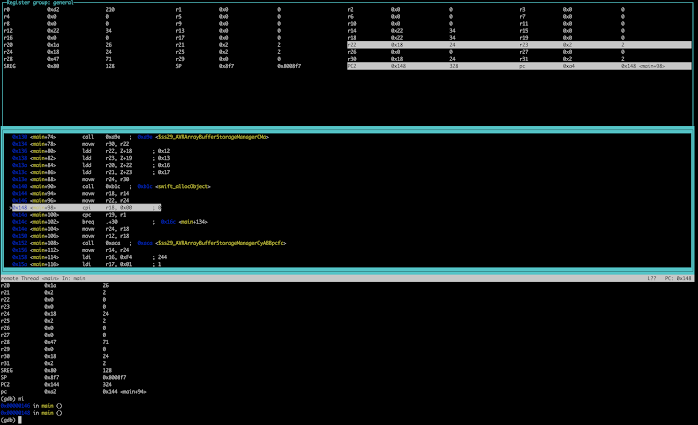
Using the "open folder" project structure, save work into a folder and build, the "Terminal" button enables. Press it and you're in a terminal session within the folder, with a command line build ready to go. Run "make simulate-gdb" and you have the program running on simavr, with the debug port open for avr-gdb to attach to. Create a separate Terminal window with the same button for your avr-gdb session and run "avr-gdb main.elf" to pick up the image symbols. In the session choose "target remote :1234" and you're in! My preferred run mode for avr-gdb is "layout asm" or "layout reg" (seen here). Obviously it's not for a beginner, but for an experienced gdb jockey it should prove interesting.
Hints
You can find these on other blogs about gdb and simavr. But might be useful here.
***
(https://sourceware.org/gdb/onlinedocs/gdb/Memory.html)
x/30xb 0x200
...will show 3 bytes in hexadecimal starting at 0x200 but there's a gotcha... gdb usually only expects one memory space, in this case you'll see the contents of "flash" memory (or its simulated equivalent). Simavr has a workaround. RAM (which is what you will usually want to inspect) "starts" at 0x800000!
For example...
(gdb) x/30xb 0x800000
0x800008: 0x00 0x00 0x00 0x00 0x22 0x00 0x22 0x00
0x800010: 0x00 0x00 0x22 0x00 0x1a 0x02 0x18 0x02
0x800018: 0x18 0x02 0x00 0x00 0x47 0x00
...dumping registers shows that is correct...
info reg
r0 0xd2 210
r1 0x0 0
r2 0x0 0
r3 0x0 0
r4 0x0 0
r5 0x0 0
r6 0x0 0
r7 0x0 0
r8 0x0 0
r9 0x0 0
r10 0x0 0
r11 0x0 0
r12 0x22 34
r13 0x0 0
r14 0x22 34
r15 0x0 0
r16 0x0 0
r17 0x0 0
r18 0x22 34
r19 0x0 0
r20 0x1a 26
r21 0x2 2
r22 0x18 24
r23 0x2 2
r24 0x18 24
r25 0x2 2
r26 0x0 0
r27 0x0 0
r28 0x47 71
r29 0x0 0
r30 0x18 24
r31 0x2 2
SREG 0x80 128
SP 0x8f7 0x8008f7
PC2 0x148 328
pc 0xa4 0x148 <main+98>
(remember the first 32 bytes of RAM on AVR map to the 32 registers r0-r31)
***

Comments
Post a Comment